thick client testing owasp|owasp top 10 scanner : factory Companies should adopt this document and start the process of ensuring that their . WEBDracula Awakening, da Red Tiger, oferece alternativas diferentes para jogadores que estão dispostos a fazer de tudo pelas suas recompensas. Prepare-se para os ventos gelados .
{plog:ftitle_list}
web20 de ago. de 2021 · OnlyFans: de imagens sensuais a sexo explícito, brasileiros contam como ganham dinheiro se exibindo. Especialistas em moderação de conteúdo e em proteção infantil dizem que isso mostra .
The OWASP Thick Client Project is a standard awareness document for developers and security analyst. It represents the most common security risks identified in thick client applications. .The OWASP Thick Client Application Security Verification Standard (TASVS) .Companies should adopt this document and start the process of ensuring that their .
The OWASP Thick Client Application Security Verification Standard (TASVS) Project aims to establish an open standard for securing thick client applications.OWASP Based Checklist 🌟🌟. 80+ Test Cases 🚀🚀. Notion link: https://hariprasaanth.notion.site/THICK-CLIENT-PENTESTING-CHECKLIST-35c6803f26eb4c9d89ba7f5fdc901fb0. INFORMATION GATHERING. Companies should adopt this document and start the process of ensuring that their .
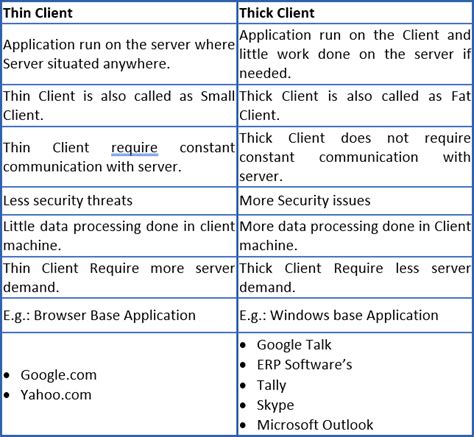
A thick client, also known as Fat Client is a client in client–server architecture or network and typically provides rich functionality, independent of the server. In these types of . Understanding Thick Client Application Security Testing. Types of Thick Client Penetration Testing. 1. Data Storage and Privacy Testing. 2. Network Communication Testing. 3. Code Quality Testing. 4. Backend API .
This post highlights different tools and approaches for testing thick client applications for vulnerabilities. Thick client testing tools have remained the same over time while new frameworks / technologies have given rise to new . To test a thick client application the most important task is intercepting the requests fired by the application. On the basis of this benchmark, it can be classified as follows: 1..The OWASP Thick Client Project is a standard awareness document for developers and security analyst. It represents the most common security risks identified in thick client applications. .
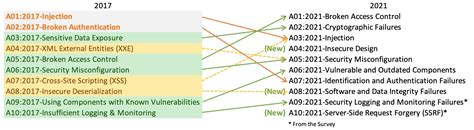
top 10 owasp vulnerabilities
OWASP ZAP; Zoom; Desktop games; Music Player; Text editor; Common Architectures of Thick Clients. Two Tier; Three Tier; Two Tier: The two-tier is based on Client-Server architecture. The two-tier architecture is like a . Common examples of thick client applications are video games, audio video editing tools, Microsoft Office, etc. Thick client security assessment can be divided into below four major parts. Static test Architecture. Thick client applications can follow various architectural models, with the most common being: 2-Tier Architecture. Client (Presentation Layer): The client application runs on the user’s machine, handling the user interface and some processing. Database Server (Data Layer): The server manages the database, responding to client queries and storing data. We use them daily in the form of web browsers, games, desktop music players, messenger programs, video conferencing tools like Zoom, etc. In simple terms, Thick Client Applications are Desktop applications based on the client-server architecture. The other definition of Thick Applications is the CLIENT in the Client-Server Architecture.
SecureLayer7 begins its thick client application pen testing service by understanding each application's intricacies and functionality. The methodology involves reverse engineering to identify hard-coded secrets, authentication weaknesses, insecure data handling, and potential client-side exploits like buffer overflows and injection attacks .The current team has pulled together the following Candidates for the OWASP Top 10 Client-side Security Risks. After a suitable comment period on this list, we’ll produce a complete draft Top 10 later in 2022 for another round of comments. Like other OWASP Top 10s, we plan to produce PDF, Wiki and/or GitBook versions of the final document so .
Our application penetration testing follows a structured methodology based on industry standards such as the OWASP Testing Guide, PTES (Penetration Testing Execution Standard), OSSTMM (Open Source Security Testing Methodology Manual), OWASP Mobile Security Testing Guide (MSTG), and NIST SP800-115.
Thick client pen-testing examines how an application manages data storage and privacy. Security specialists analyze whether sensitive information is appropriately encrypted and securely kept, as well as if access restrictions are in place to prevent unauthorized access to personal data. . OWASP TOP 10 Rank; SANS Top 25 Rank, and; References . Thick clients are the applications that must be installed on desktops/laptops or servers. These applications can be run on the internet or without the internet. The most common example of a thick client is the installer Skype installed on the desktop/laptop. Other examples of Thick Client are Firefox, Chrome, Microsoft Teams, Zoom, etc. Thin clients.The client application to connect using TLSv1.2+ with modern ciphers (e.g, AES-GCM or ChaCha20). The client application to verify that the digital certificate is correct. The Transport Layer Security Cheat Sheet contains further guidance on securely configuring TLS. Configuring Secure Authentication¶
OWASP ZAP, on the other hand, focuses on web application security and provides a comprehensive set of tools for testing thick client applications. Its automated scanning capabilities help identify common vulnerabilities, such as cross-site scripting (XSS) and SQL injection, in both the client-side and server-side components of the application. Let’s explore few more concepts Standalone Thick Clients vs Networked Thick Clients. 1. Standalone Thick Clients: Operate independently of a network. Example: Microsoft Word, Adobe Photoshop.
Burp Suite/OWASP ZAP — can be used for dynamic application security testing. MitmProxy — is an interactive, SSL/TLS-capable intercepting proxy with a console interface for HTTP/1, HTTP/2, and .Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and practical methodology for thick client Pentesting. Whether you're .
thick client pentest checklist
Proxy unaware thick client: Do not natively include proxy settings so the user is required to make some changes in the system’s host file Thick Client Testing Methodology. Currently, there is no definite methodology when . How to test thick client applications? 👨💻. Thick Client Pentest is complicated as compared to /API Pentest in my opinion. In Thick Client, there are two types (i) Proxy-based Thick clients. (ii) Non-Proxy based thick . Thick client applications can be developed using Java, .Net, C/C++, etc. A thick client may follow two-tier architecture or three-tier architecture. . Thick Client Security Testing - Short Tutorial. . OWASP .Though, thick client applications are not new, penetration testing process for thick clients is not as straight as Application Penetration testing. It is commonly seen enterprises using thick client applications for their internal operations. Even today, we can find a lot of legacy thick client applications being used by big companies.
OWASP Foundation Respository. Contribute to OWASP/www-project-thick-client-security-testing-guide development by creating an account on GitHub.The OWASP Thick Client Project is a standard awareness document for developers and security analyst. It represents the most common security risks identified in thick client applications. Organizations should adopt this document to ensure that their applications minimize these common risks. Using the . Diagram 1.2 (3) the thick client can be divided into two parts as shown below: (3.1) exe files or (3.2) web-based launcher like a java-based application.
The choice between thick clients, thin clients, or web applications depends on the specific requirements and constraints of a given project or application. The following is a complement from HTB Academy. Thick client applications can be categorized into . Thick Client Penetration Testing; VoIP Penetration Testing; On Demand Penetration Testing; CODE AUDIT; Ethereum Smart Contract Audit; Source Code Audit; SECURITY EXPERTISE. . If followed meticulously, this OWASP’s Top 10 testing principles complete checklist should allow you to reduce operational failures, application errors, .6.1.1 Security Testing Guide. The OWASP Security Testing Guide (WSTG) is a comprehensive guide to testing the security of web applications and web services.. The WSTG documentation project is an OWASP Flagship Project and can be accessed as a web based document.. What is WSTG? The Security Testing Guide document is a comprehensive . The OWASP Top 10 includes a number of tests that are applicable to thick client applications. In addition, the OWASP provides associated tools and information. One of the most important tools for testing thick client applications is Echo Mirage. This tool can help you intercept and manipulate TCP traffic on a remote computer.
The OWASP Testing Guide chapter on SSL/TLS Testing contains further information on testing. There are a number of online tools that can be used to quickly validate the configuration of a server, including: . However, public key pinning can still provide security benefits for mobile applications, thick clients and server-to-server communication. OWASP Top 10 : Cross-Site Scripting #3 Bad JavaScript Imports August 28, 2017. August 6, 2017. Static Analysis/ Reverse Engineering for Thick Clients Penetration Testing 4. Hi Readers, let’s take a look into static analysis. The advantage which thick clients offer over web applications are the ability to inspect the code and perform code .
how hard is the vtne test
how hard is the w3 html test
webStrength + mixed with volume = well developed legs. #fittips #fitness #glutes #workout #fyp. Miranda Cohen (@mirandacohenfit) on TikTok | 38M Likes. 3.1M Followers. 👻 Ghost .
thick client testing owasp|owasp top 10 scanner